 | Appendix A: Security Tools |  |

The last security-related tool that comes with the Java platform is policytool. This tool allows you to manage entries in a java.policy file. Unlike the other tools we've discussed, policytool is a graphical tool. As such, it has no command-line options or arguments.
When you first start policytool, you see a blank window with two pull-down menus: File and Edit. Initially, there are no policy entries loaded into this tool; if you want to work on an existing policy file, the first thing you must do is choose the Open command from the File menu. Otherwise, you can add new entries and create a new file containing those entries. Whichever method you choose, keep in mind that policytool is designed to operate on a single policy file.
When you've completed editing the entries for a policy file, you can save your changes. Under the File menu, you can use the Save or Save As command to overwrite the file you loaded or to save your changes to a new file.
The initial screen for this tool displays the name of the currently loaded policy file (which is blank if no file has been loaded); the name of the keystore referenced within this file; buttons to add, edit, or remove policy entries; and a list of the current set of policy entries. In this context, a policy entry is the URL from which classes will be loaded; that is, a codebase or a code source. Hence, a single policy entry may contain many individual permissions. In Figure A-1 we've loaded the default java.policy file, which has one policy entry: an entry that grants permissions to all codebases.
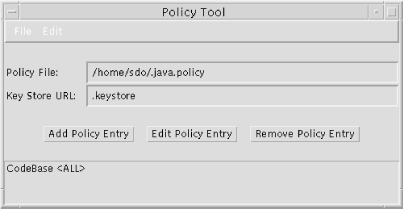
Note that the keystore entry for this file is .keystore. You can change that value through an option under the Edit menu.
You can add new codebases to this file by selecting the Add Policy Entry button; when you add a policy entry, you are allowed to specify a URL and a signer (both of which are optional). The entry for the signer should be an alias in the keystore; if you enter a signer who is not in the keystore, you'll get a warning, but the operation will continue.
You may delete codebases by selecting one and pressing the Remove Policy Entry button. Selecting a codebase and pressing the Edit Policy Entry button allows you to edit the specific set of permissions for a codebase.
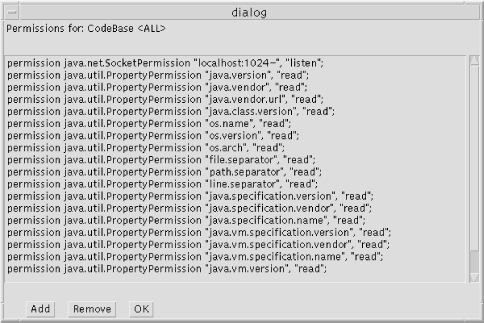
When you press the Edit Policy Entry button, you get a window similar to that shown in Figure A-2. This window lists all permissions that are associated with the given codebase, and provides the opportunity to add or remove individual permissions.
Policytool also allows you to perform some rudimentary operations on the default keystore (again, using whatever KeyStore class implementation has been installed into your Java platform). Under the Edit menu, there are options to add and remove public key aliases. These public key aliases are certificate entries in the keystore. In order to add an alias, you must specify a name for the alias and the name of a file containing a certificate (in RFC 1421 format) to import for that alias; you may remove an alias simply by name.

Copyright © 2001 O'Reilly & Associates. All rights reserved.